With v12 it will be supported to use group Managed Service Account (gMSA) for user credentials.
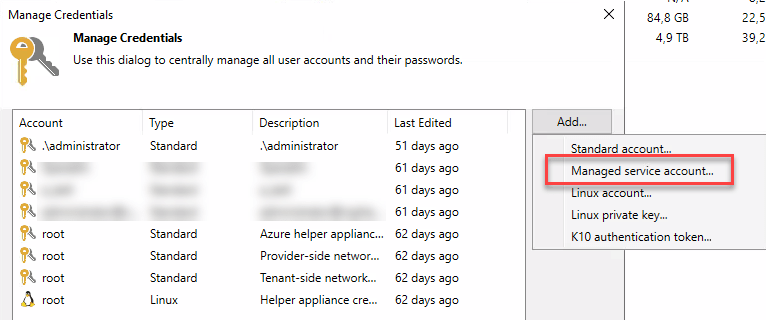
For my understanding of gMSA it will be necessary to have VBR server in a domain. Because it will still not be recommended to join this server the production domain, a special resource or management domain could be needed. For more details we will have to wait for general availability to get the user guide.
If you have more ideas about gMSA implementation, let us know 😀











