THERE IS NOW NATIVE FUNCTIONALITY TO DO THIS EASILY
Greetings everyone, Audit Logging always is an interesting topic, it doesn’t matter if you need this due to compliance, or just for best practices. Having visibility of restore operations of something as critical as emails, documents, etc. should be a must.
When I am mentioning the word Audit, I am talking about all the Restore operations that anybody does using the Explorers, PowerShell, or API, or even using the new Restore Portal (meaning opening an email, restoring it, saving it, etc.)
As we stand today, we have the next methods to Audit the Restore Operations:
- Inside the Veeam Backup for Microsoft 365 Console, under History - Restore
- On Windows Logs, on the Client who opened the Console and Explorers (bear this in mind)
- RESTFul API can send real-time alerts
- RESTful API to obtain RestoreSessions with extreme great detail
- Windows Logs to parse some Infrastructure actions like Job Creation, Edit, Deletion, etc.
Advanced VB365 Audit
PowerShell audit - Some visibility
Let’s start with PowerShell. Veeam Backup for Microsoft Office 365 includes a feature-rich PowerShell toolkit (you can learn about every single cmdlet on the next Help Center). As we’re trying to get an advanced reporting or audit, let’s go and take a look at Get-VBORestoreSession first. This cmdlet is quite simple to use, and it will show us the details on a specific restore session, like when it was initiated, by whom, status, etc.
Get-VBORestoreSession -Id beaa5ce4-f0bb-46c7-aafb-1c4c4df40757
Id : beaa5ce4-f0bb-46c7-aafb-1c4c4df40757
Name : Exchange restore (Job: BJ-EXCHANGE-ALL1 - 9/28/2020 4:00:13 PM)
StartTime : 9/28/2020 4:20:45 PM
EndTime : 9/28/2020 4:23:48 PM
Status : Stopped
Result : Success
Type : Exchange
InitiatedBy : VEEAMVBO3\Administrator
ProcessedObjects : 70Windows Logs - Some visibility
Logs produced on the Client who opens the Console/Explorers
Veeam has Windows Logs as well, yes of course we do. You can find them under C:\ProgramData\Veeam\Backup\* there are folders here for every Explorer.
In some of the logs you can find the next, which means, who opened the console, IP, etc. And a basic log of what this person has done:
[20.04.2022 11:45:45] 1 (7436) Server: VEEAMVBO3 (CPUs: 8, RAM: 18.0 GB)
[20.04.2022 11:45:45] 1 (7436) Network:
[20.04.2022 11:45:45] 1 (7436) IPv4: 192.168.1.32, IPv6: fe80::d025:90d2:90fe:58ce%8, Adapter: Ethernet0
[20.04.2022 11:45:45] 1 (7436) IPv4: N/A, IPv6: N/A, Adapter: isatap.{99D11A50-110F-40AD-93A8-DAF20BAFB5A4}
[20.04.2022 11:45:45] 1 (7436) IPv4: N/A, IPv6: 2001:0:2851:782c:442:2bc7:3f57:fedf, fe80::442:2bc7:3f57:fedf%14, Adapter: Teredo Tunneling Pseudo-Interface
[20.04.2022 11:45:45] 1 (7436) OS: Microsoft Windows NT 10.0.14393.0 (x64)
[20.04.2022 11:45:45] 1 (7436) UTC Date & Time: 4/20/2022 10:45:45 AM
[20.04.2022 11:45:45] 1 (7436) Timezone: (UTC+00:00) Dublin, Edinburgh, Lisbon, London
[20.04.2022 11:45:45] 1 (7436) Daylight: GMT Daylight Time
[20.04.2022 11:45:45] 1 (7436) Account: VEEAMVBO3\Administrator
[20.04.2022 11:45:45] 1 (7436) Log level: Extended (size fidelity: 256, size limit: 10485760, files limit: 16, archives limit: 128)
[20.04.2022 11:45:45] 1 (7436) ================================================================================
[20.04.2022 11:46:21] 20 (6856) Microsoft Exchange Web Services binding path: https://outlook.office365.com/EWS/Exchange.asmx
[20.04.2022 11:46:21] 20 (6856) Opening root folder using impersonation...
[20.04.2022 11:46:21] 20 (6856) Opening mailbox (user: jorge.delacruz@jorgedelacruz.es)...
[20.04.2022 11:46:22] 20 (6856) Root folder opened successfully
[20.04.2022 11:46:22] 20 (6856) Exchange Web Services initialized
[20.04.2022 11:46:22] 20 (6856) Connection a296c01d-bfe3-4a3a-932f-a75d40e7ce01 is closed
[20.04.2022 11:46:22] 1 (7436) Restore configuration:
[20.04.2022 11:46:22] 1 (7436) Use specified account: jorge.delacruz@jorgedelacruz.es
[20.04.2022 11:46:22] 1 (7436) Restore to original folder: True
[20.04.2022 11:46:22] 1 (7436) Restore changed items: True
[20.04.2022 11:46:22] 1 (7436) Restore deleted items: True
[20.04.2022 11:46:22] 1 (7436) Mark restored items as unread: True
[20.04.2022 11:46:22] 1 (7436) Use specified Exchange server: outlook.office365.com
[20.04.2022 11:46:22] 11 (13860) Initializing Exchange Web Services...
[20.04.2022 11:46:22] 11 (13860) Connecting to Exchange Web Services (server: outlook.office365.com, account: jorge.delacruz@jorgedelacruz.es, ID: 45040713-d1a5-41ff-88b5-fcf86c8a9b7b)...
[20.04.2022 11:46:22] 11 (13860) Microsoft Exchange Web Services binding path: https://outlook.office365.com/EWS/Exchange.asmx
[20.04.2022 11:46:22] 11 (13860) Opening root folder using impersonation...
[20.04.2022 11:46:22] 11 (13860) Opening mailbox (user: jorge.delacruz@jorgedelacruz.es)...
[20.04.2022 11:46:22] 11 (13860) Root folder opened successfully
[20.04.2022 11:46:22] 11 (13860) Exchange Web Services initialized
[20.04.2022 11:46:22] 11 (13860) Counting items...
[20.04.2022 11:46:22] 11 (13860) found 1 item(s)
[20.04.2022 11:46:22] 11 (13860) Restoring items...
[20.04.2022 11:46:23] 11 (13860) Item skipped: Item (class: IPM.Contact)
[20.04.2022 11:46:23] 11 (13860) Restore completed for: items (restore time: 00:00:00.7970556)
[20.04.2022 11:46:23] 11 (13860) skipped 1 item(s)
[20.04.2022 11:46:23] 11 (13860) created 0 item(s)
[20.04.2022 11:46:23] 11 (13860) merged 0 item(s)
[20.04.2022 11:46:23] 11 (13860) failed 0 item(s)
If possible, you should be parsing these logs with Splunk or Elastic, and build some stuff. It has some caveats:
- Not enough detailed information about what items are restored in my opinion
- You can only have these logs on the Client who is doing the restore, the one opening the Console and Explorers. (Meaning either you have a jump box you control, of you parse logs from people PCs, which seems hard)
RESTful API - Full visibility
Real-time Email alerts to a Security Distribution List
Veeam Backup for Microsoft Office 365 v5 introduced Microsoft Teams Protection and Scalability enhancements. But at the same time, a native enhanced Audit per Restore Operation was released as well, but it could only be enabled by leveraging the RESTful API. I wrote a very comprehensive step-by-step that can be found here on how to enable it.
Audit diagram in Veeam Backup for Microsoft Office 365 v5
Before we briefly start with the subject, I think a diagram about how this new way of auditing works can help us better understand what we are going to do, and activate:

A practical example of an audit being sent in real-time
As I say, no matter if we open the Explorer from the server, from a Tenant, or from another PC. Any element that the Backup Admin opens, restores, or exports, the relevant security email will be sent so that everything is audited, for example, I have opened an Exchange Explorer, and in a user where the audit is enabled I have decided to export an email to my computer as .msg: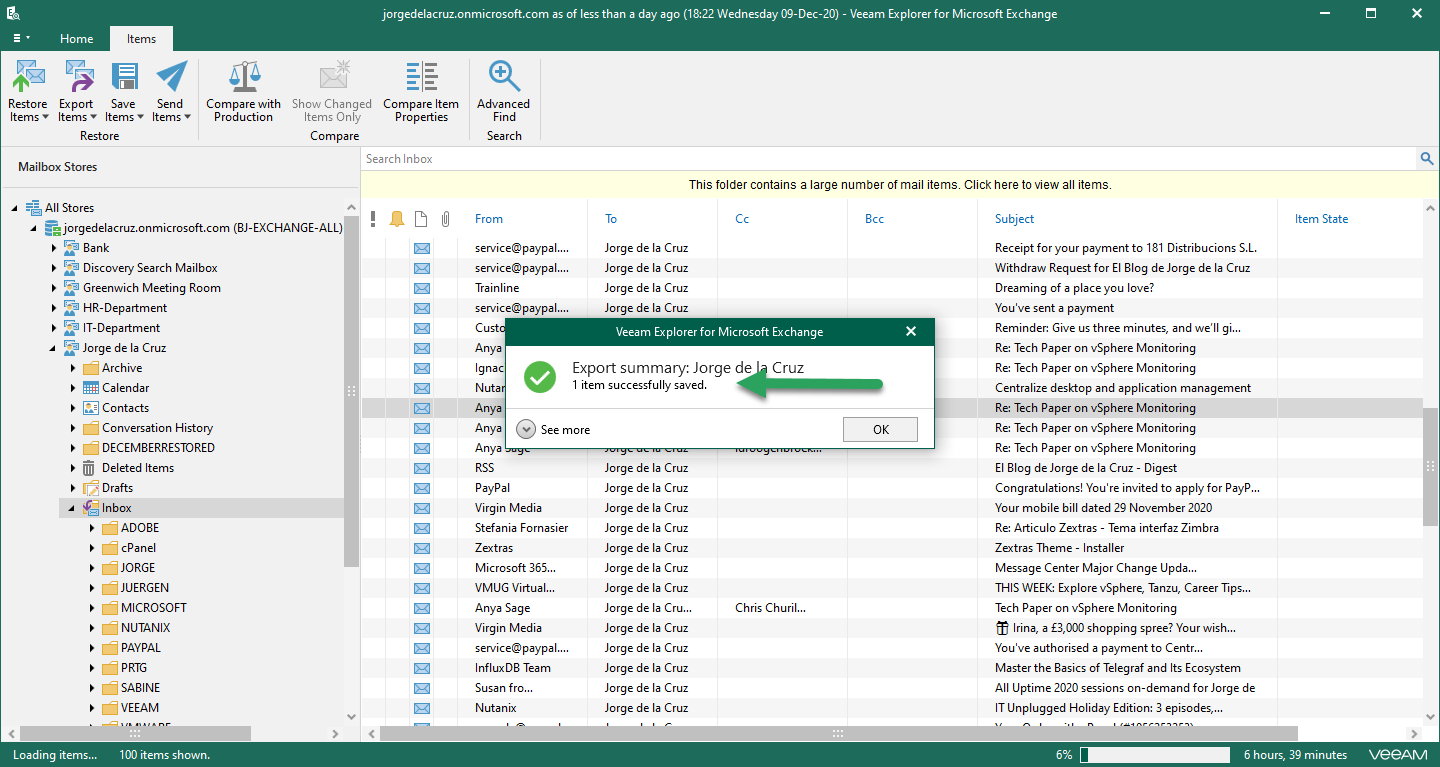
I have immediately received this message in my security account where I am auditing who does what and when, and in this case where I have exported the item: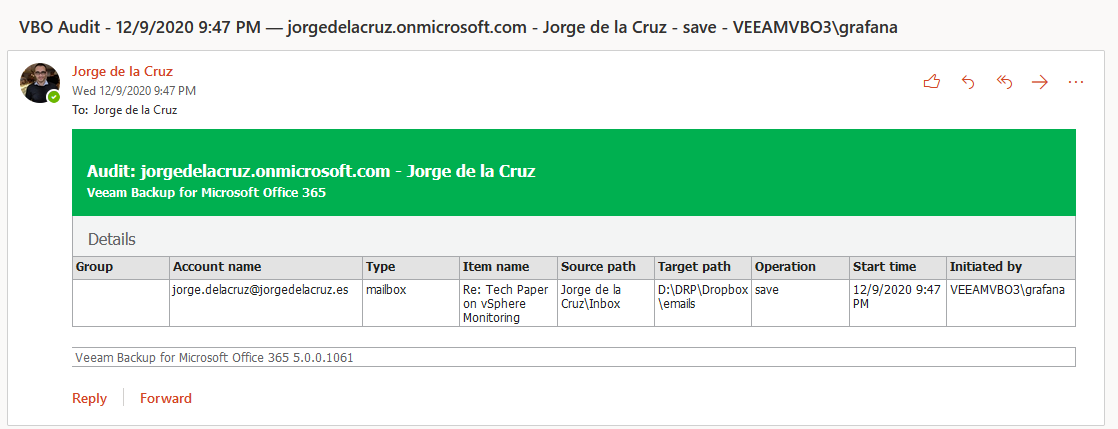
An absolute hidden gem, that with just a few steps can be enabled for your Veeam Backup for Microsoft Office 365.
Enhanced in Veeam Backup for Microsoft 365 v6 / Full Detailed RestoreSession
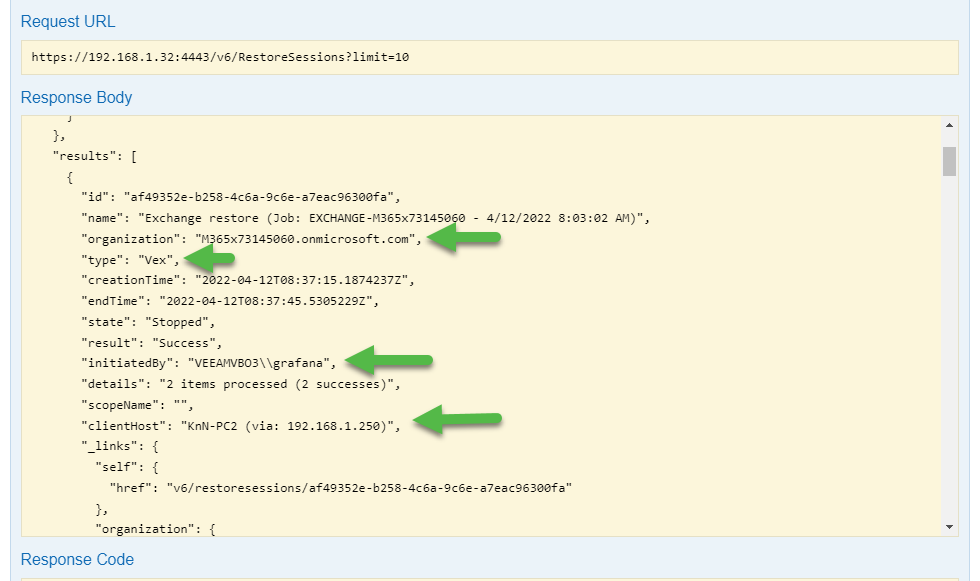
Including in VB365 v6, we can find the RestoreSessions/ID/events endpoint that gives us extreme detail of what happened on that particular restore session, could be using Explorers, Restore Portal, or API, it doesn't matter.
For example, when we call the RestoreSessions, we already have some useful data like:
- Organization
- What kind of restore it was, Explorer for Exchange, Portal, etc.
- Who initiated this Restore Session
- Client Host IP, is really useful if using the console on external computers (Restore Portal will show 127.0.0.1 + the original IP from the User)
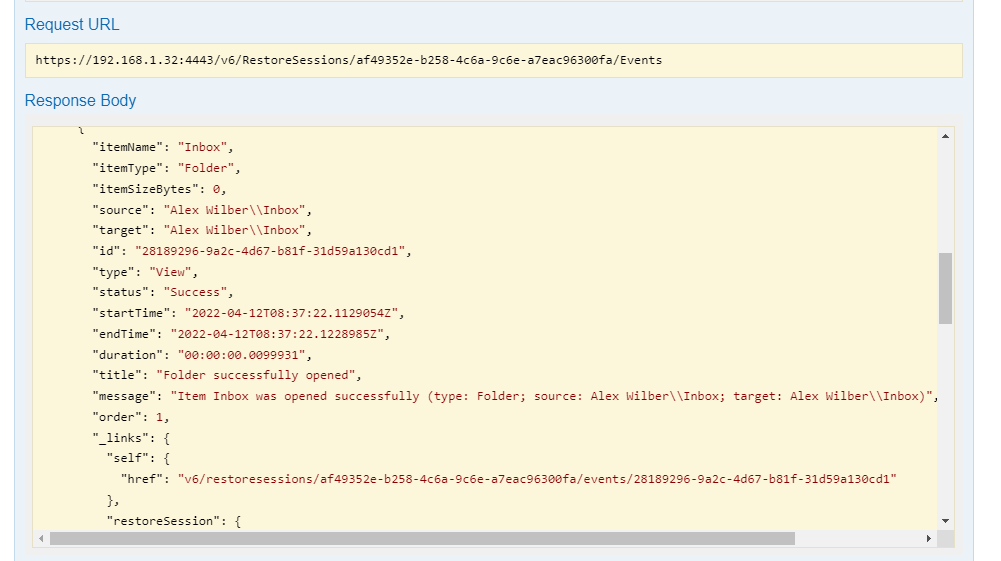
Powerful already, but still some more magic left. Now, let's use the RestoreSessions/ID/Events, where we can see:
- ItemName, Type, Bytes, etc.
- The action the Restore Operator did, in this case just "View"
- Enhanced Message with all actions that had happened
- Source and Target
You get the idea, with these two RESTful API Endpoints you can build whatever you like, send them to InfluxDB and consume them on Grafana, or create your own HTML Reports on demand, etc.
As an example, find this great dashboard consuming these very API endpoints:
Dark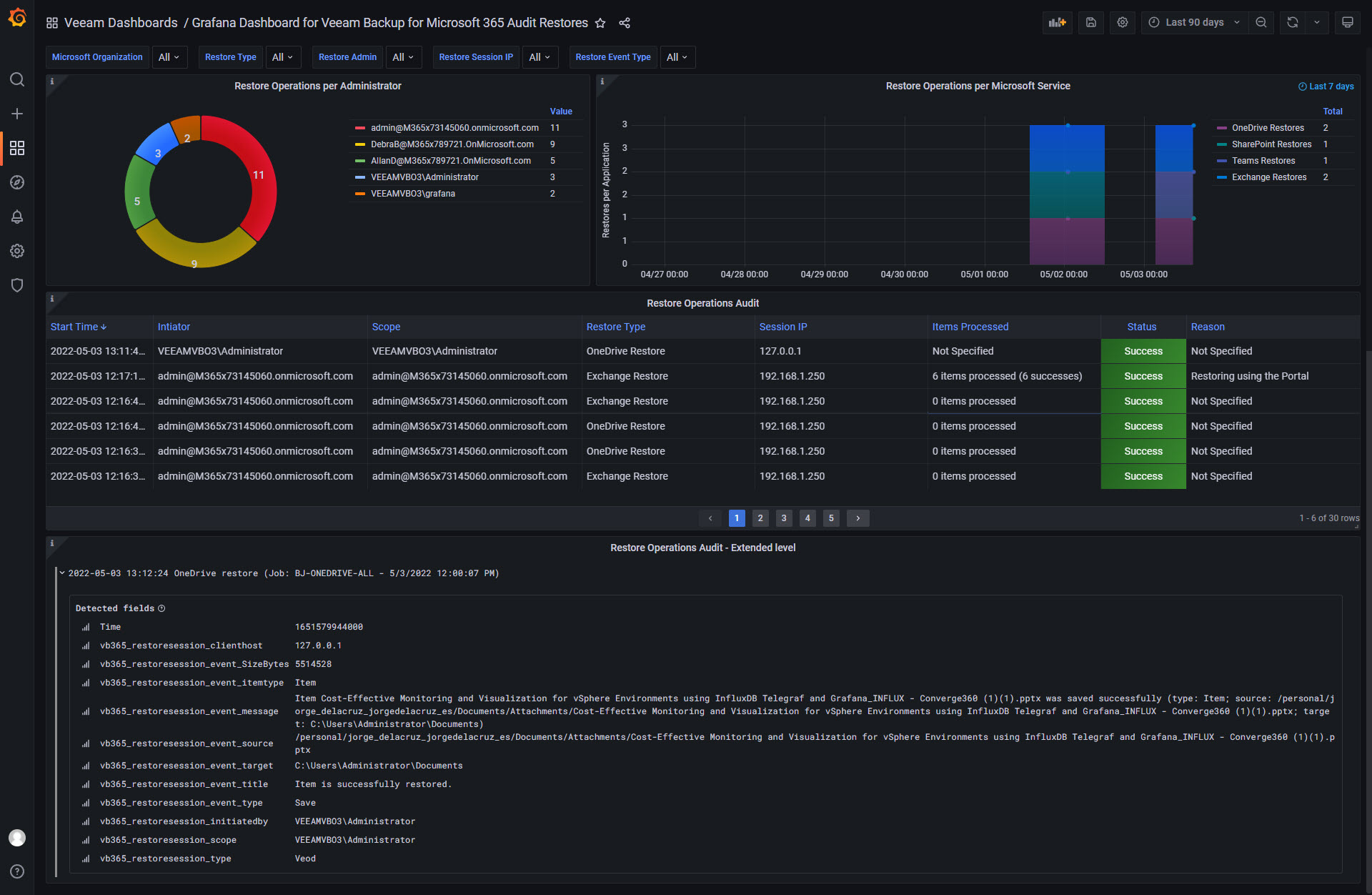
Light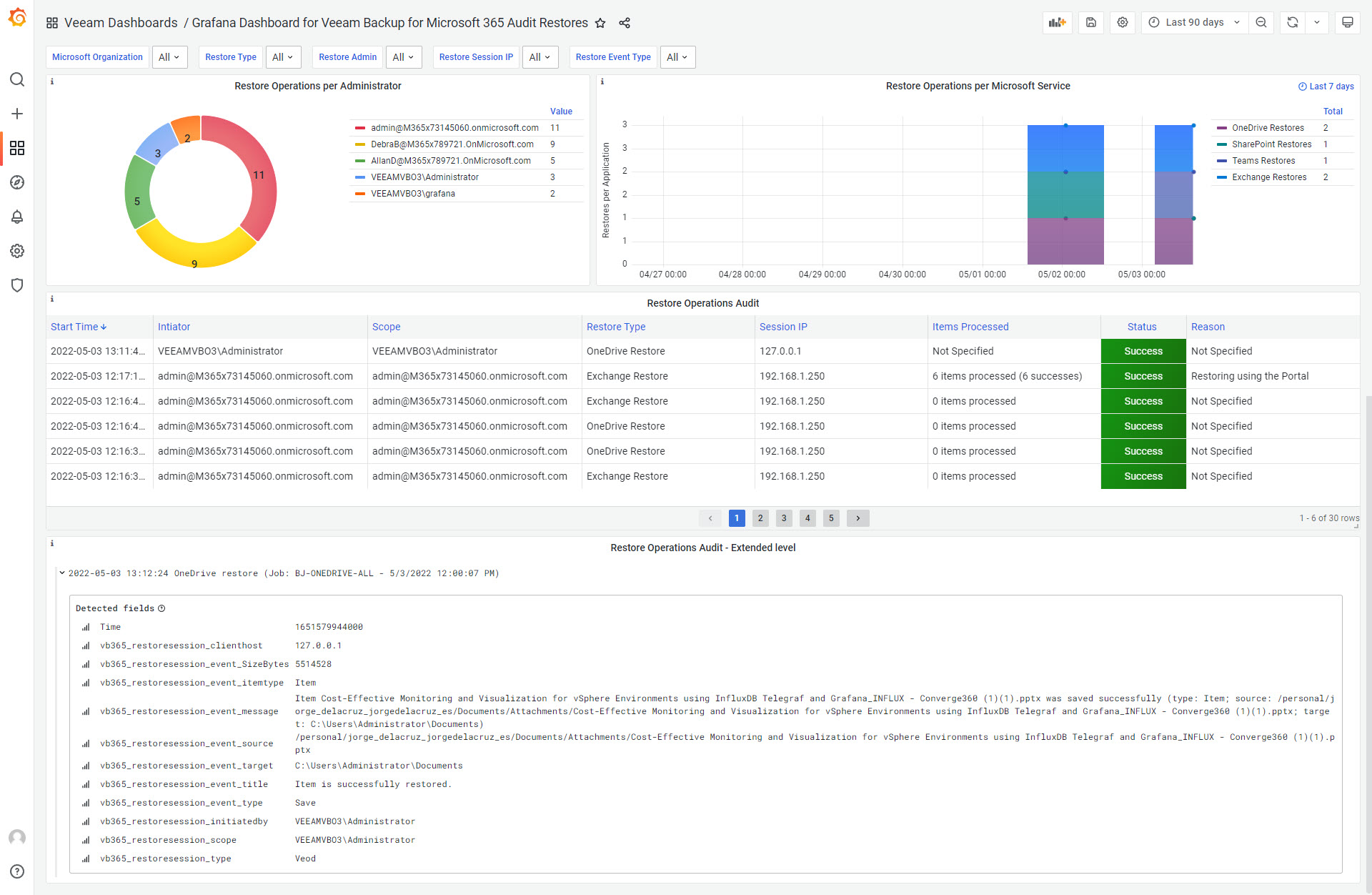
Log Parsing - Next-Gen
RBAC visibility on which Admin has done what on Infrastructure
Veeam Backup for Microsoft 365 has a log called C:\ProgramData\Veeam\Backup365\Logs\Veeam.Archiver.Shell*.log where all the actions to the platform are stored, meaning who creates jobs, who edit them or deletes them. It is very early days on this, but you can do some magic with Grok and build a Dashboard similar to this:
Closing thoughts
I hope you got everything you need in order to detailed monitoring of all the actions, outside the VB365 Console. My total favorite is the RESTful API in v6 with that level of detail. But thinking practically, the SMTP Notification to a Security Distribution List to me seems the most practical really.
Give this a few reads, as I understand it has a lot. Hope it helps. Please ping me if you need more information.