Quite a cool new feature is the ability to enable Multi-factor authentication (MFA) for the VBR console login.
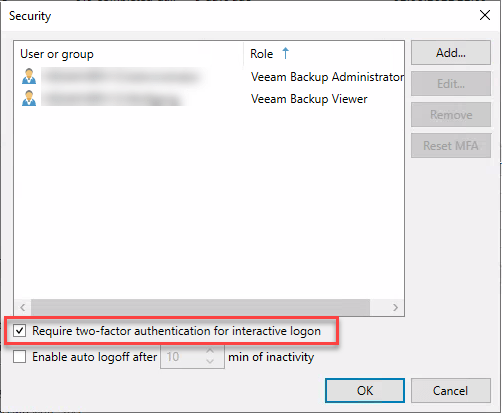
With this a user has to enter username, password and an additional confirmation code that comes from a Authenticator app like Google Authenticator.
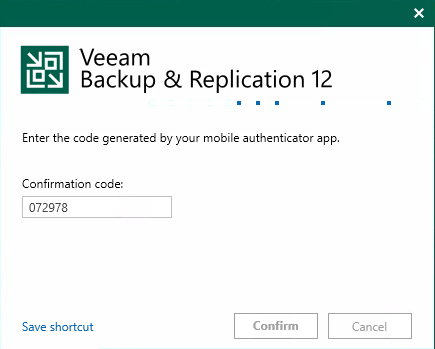
At first login, User can add VBR to his Authenticator app.

It is really simple to use.
BUT: 2FA works only for VBR console, NOT for PowerShell!
Another security improvement is the option for Automatic Session logoff:






