It is always interesting, when thinking of special situations, to ask: What happens, when …
Here are the answers to at least a few of these questions ![]() - for immutable backups in VBR v11:
- for immutable backups in VBR v11:
What happens, when…
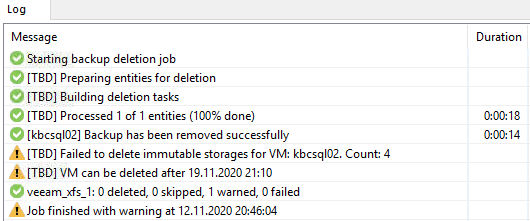
… removing immutable restore points?
Task starts and ends up with errors. No restore point is removed.
… hacker changes date/time on Veeam server to remove files with next backup run?
Excellent question! But it will not work! Configured period of time is checked at Linux server, not at Veeam B&R Server! So a job running one year in the future will create new files, it cannot delete old ones.
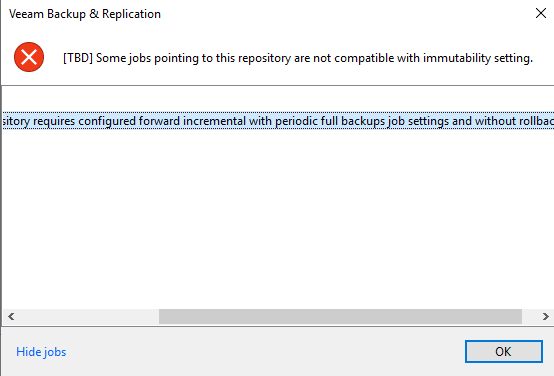
… enabling feature at existing repository, not compatible with hardened repository?
Veeam checks if there are backup jobs configured with an incompatible backup chain. If found, error is shown:
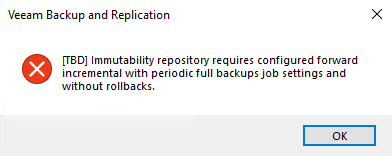
… changing a backup job writing to immutable repository?
When backup chain is changed to an incompatible one, error is shown:
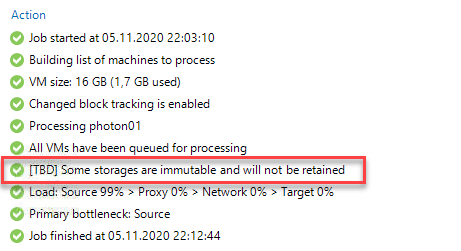
… days for immutability is higher than the number of restore points?
Restore points are kept to the end of the period, defined for immutability. Notice that there is an information message in job log:
… immutability turned on on repository containing restore points?
In this case immutable flag is set on all files, according immutability period.
… immutability turned off on repository containing immutable backups?
In this case, immutable flags are kept. That makes perfect sense. Otherwise a hacker with backup administrator permissions could disable hardened repository to delete backup files. Notice: new backups are not immutable after disabling the feature.
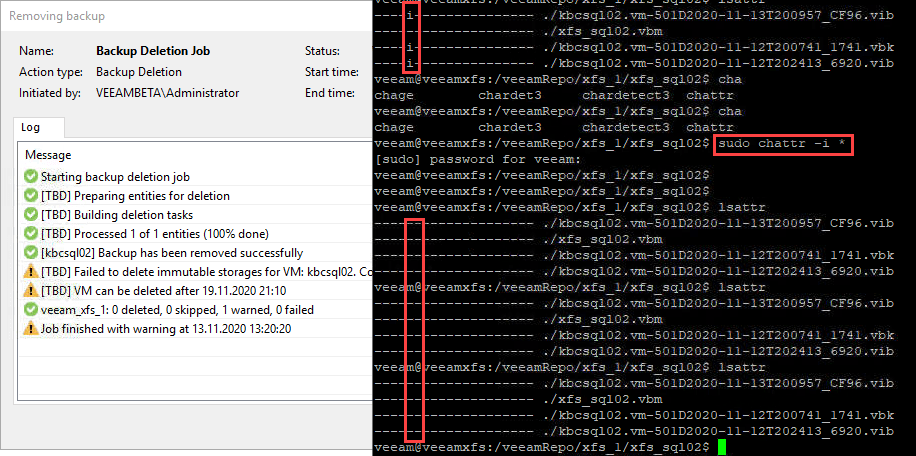
… trying to remove restore points in GUI on files with immutable flag manually removed?
Interestingly files will not be deleted! Probably because Veeam knows, files should be protected. There will be more details on that after the release of v11.
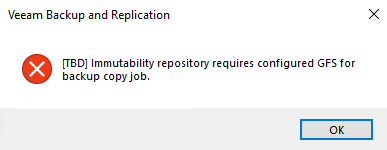
… use immutable repository as target for copy job without GFS?
Backup copy jobs requires GFS when copied to immutable repository. If no GFS is set up, error appears.